SQL Server Security Best Practices Checklist- All You Need to Know
Microsoft SQL Server database is one of the most widely used solutions present nowadays for users. However, due to the rapid increase in SQL attacks & security malfunctions, users must be aware of the MS SQL Server security best practices checklist. Hardening the security parameters is a must in this era of a virtually expanding world.
This blog is focused on providing users with the most refined SQL Server security checklist. Evidently, Here, we’re going to discuss what to avoid, types of security requirements, column & row level protection, disaster management solutions, & much more.
Avoid MS SQL Threats for SQL Database Security Best Practices
SQL Server also have a high susceptibility of getting threats that might cause severe damage to the crucial data files present in them. Evidently, it’s quite a responsibility for DBAs to make sure their servers are secured & they are following all the SQL Server hardening best practices in advance. Below we have mentioned some of the most interesting & popular threats to SQL Server DB including old ones to the latest ones.
Chances of SQL Injection Attacks: An SQL attack on a database by planting malicious code in the SQL queries. This malicious code returns in the form of an error or some crucial information that the attacker might misuse.
Physical Damage to the Database: It’s equally important for DBAs to protect the physical server as unauthorized people might harm the physical database, steal storage drives, or do some other damage even by accident.
High Level of Database Abusing: An attacker might use the database’s vulnerabilities to penetrate through it& get total control over it. Thus, frequent monitoring & auditing is kind of a necessity by the DBAs for MS SQL security best practices.
Preventing Unauthorized Access: To stop cyber criminals from brute-forcing passwords, DBAs must take action forbidding unauthorized access. Also, increasing the Authorization security can be an ideal initiative.
Hyped Privileges of SQL Server: When an attacker uses the loopholes in the database to increase his/her privileges & benefits, DBAs must understand that someone has hyped privileges of the databases. Thus, they must harden SQL Server security best practices.
Also Read: How to Reset the Password in SQL Server? Effectively
Types of SQL Server Security – Unlocking All the Realms
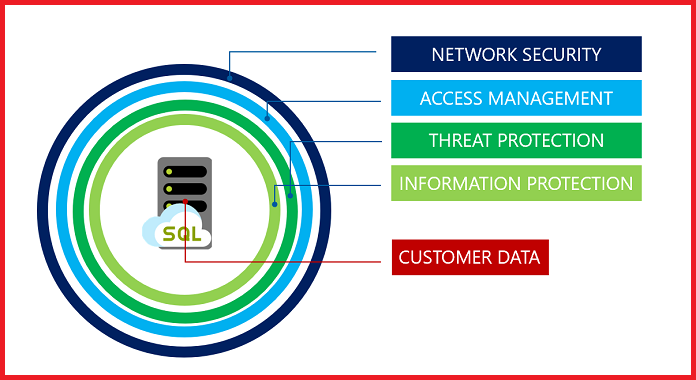
SQL Server security is a very broad term & users need to focus here on segments. Therefore, we have divided the security into 5 different sectors. Each of these security practices demands focus & almost no scope for any kind of error. While learning the SQL Server security checklist, users can not miss out on any of these points at all.
#1 SQL Server Security Best Practices for Physical Server
Users must restrict their physical server from unnecessary people who might even have the slightest chance of harming them. This includes complete protection for the hardware components with multiple layers. Locked Server rooms, restricted access, 24✖7 monitoring, etc. Restricting the backup media access is also crucial by keeping it in a remote location away from the reach of the majority of users.
Users should keep unwanted users away from the server by using the physical network security parameters. To Find out more on this, Go through the SQL Security for Infrastructure Threats page. Physical security is the first & most basic aspect to consider for MS SQL security best practices. Thus, users must take this seriously.
#2 Operating System & Operating System File Security
A robust & error-free operating system builds a strong foundation for maintaining SQL security standards. Therefore, users must secure their operating system using the following best practices:
- Updating the OS with the latest versions of security patches is a must.
- An active licensed anti-virus software is one of the basic security needs.
- Keep an eye on the file system to prevent corruption issues at all stages.
- eliminating the internet access on the servers is another trick to consider.
- Building robust firewalls is very significant to stop the unwanted attackers.
- Only necessary ports should be available to connect with the applications.
#3 SQL Server Password Security Practices
To address password security, we need to discuss a few more things first. Plenty of users must be aware of the option to attach SQL logins already & AD(active directory) users in the MS SQL Server for DB access. It is quite common for users to learn SQL Server security best practices.
Moving ahead, in AD, the group policies take care of password security where the AD administrator has total control over them. Still, when a user attaches a new SQL login, they get a few options for password security as mentioned:
- CHECK_POLICY: In scenarios where users have active directory policies on a system running the SQL Server, the new login has to comply with the AD policy.
- CHECK_EXPIRATION: It’s required for users to reset the password after a certain interval of periods like in the banking apps.
- MUST_CHANGE: When a user attaches a new login & enables this option, they must change the password one time after the first login to maintain integrity.
#4 MS SQL Database Security from SQL Injections
We have already discussed the threat of SQL injection. Also, by validating user inputs to scrub error output data from being an open target for the attacker, users can explore the real potential of themselves. Moreover, we have certain ways that can help users get rid of these attacks on the SQL Server & find out all the SQL Server hardening best practices easily.
- Review all the running SQL processes that might be creating some kind of SQL injection vulnerabilities.
- Advanced use of the dynamic SQL statements parametrically can help users minimize the chances of attack to a great extent.
- A few of the characters should not be taken in use:
- ;: Query delimiter
- /* … */: Comment delimiters.
- ‘: Character data string delimiter
- –: Single-line comment delimiter.
- xp_: Catalog-extended stored procedures, such as xp_cmdshell.
- Start using the SQLCLR cmd which is far better from the xp_cmdshell.
#5 MS SQL Security Best Practices for Upgrades & DB Monitoring
Just like Windows OS, Microsoft also releases upgrades on fixed periods for the users to match with the up-to-date technologies. Moreover, these Microsoft update patches also help users to keep the security features strict for all. Users should never leave the SQL Server Cumulative Update also known as the (CU) as it offers some major changes & upgrades in terms of security.
As a part of SQL database security best practices, monitoring the database 24/7 to find any suspicious event, user transaction, etc can be effective. It helps in detecting any ongoing malicious activities. It also ensures users that the database is healthy or not or requires any support.
Managing SQL Column Level Protection
Just like every table, SQL Server tables also have rows & tables. This is why, users get the opportunity to fix the security issues on both column & row levels. Let’s begin with the column level protection first as a part of the SQL Server security best practices checklist of all time.
ID Numbers, Contact Details, Addresses, Social Security Numbers, Names, Family Details, etc information are generally stored in the columns. Therefore, it is the utmost priority of users to project this information at any cost.
These are the best ways to protect such information without any hassles:
- Do not forget to enable the Always Encrypted option.
- Users must focus on randomized encryption techniques over others.
- Using the DDM or Dynamic Data Masking is another great example.
Row Level Protection for MS SQL Server Utmost Security
When we talk about the Row level protection, it is equally important for the SQL Server database security best practices. When we have a look at the rows, so there are individual data sets that can cause trouble if mismanaged. All of the tactics that users are taking in use for the column protection, can be used here.
However, Before executing any operation, users must check to see if there are any drawbacks or not. Some experts suggest that instead of separate rows & columns, users should directly focus on the security of the entire table.
All of the approaches are good enough to adapt if the users are comfortable & proficient with the technicalities & challenges. Thus, SQL Server security checklist can be easily fulfilled.
Also Read: Fix SQL Server Error 9002 without Experts’ Assitance
Intact Data Backup and Integrity
Emergencies do not knock before stepping on your door. Therefore, keep the database integrity intact with a well-maintained backup. This can help users in cases like system crashes, database deletion, severe corruption, & whatnot. The more frequent a backup is, it will recover the database with minimum data loss.
Now, backups are also of different types. To understand the SQL Server hardening best practices without issues, users need to know the value of keeping backups. These backup types include Full backup, differential backup, & other specifications.
Best Security & Disaster Recovery Solutions Available
There are some tools including both manual & others that users must have. Such tools make it easy for the users to undergo all the operations explained above. We are hoping users must be aware of a few & there are chances that they might have using them already.
- SQL Server Management Studio: MS SQL security best practices can be handled easily with SSMS. This solution is developed by Microsoft & is currently available to use for executing complex procedures.
- rskeymgmt Utility (SSRS) Solution: This utility right here can easily modify the symmetric keys for a report server without any hassles.
- SQL Server Configuration Manager: To manage the entire control of the SQL Server, & configure network & other settings, the configuration manager is the best solution from Microsoft.
- Third-Party Solutions: For tasks, like recovery, repair, and analysis, users can trust a few solutions that are perfectly suited for SQL operations. SQL database recovery, T-Log Analyzer, etc are some examples.
- The SQL Server CMD Line Interface: We are all aware that if we are talking about SQL, then we can’t forget the command line interface to get all the tasks done. Also, users can use the commands through SSMS.
- Policy-based Mgmt. Administer Server: This utility simply allows users to manipulate the symmetric keys for a remote server.
Conclusion
We hope that now users are well aware of the SQL Server security best practices checklist. It’s obvious that users need to take care of plenty of factors as the SQL database itself is very dynamic & vast. However, with the techniques mentioned above, SQL Server hardening best practices are not a tough task for SQL users.